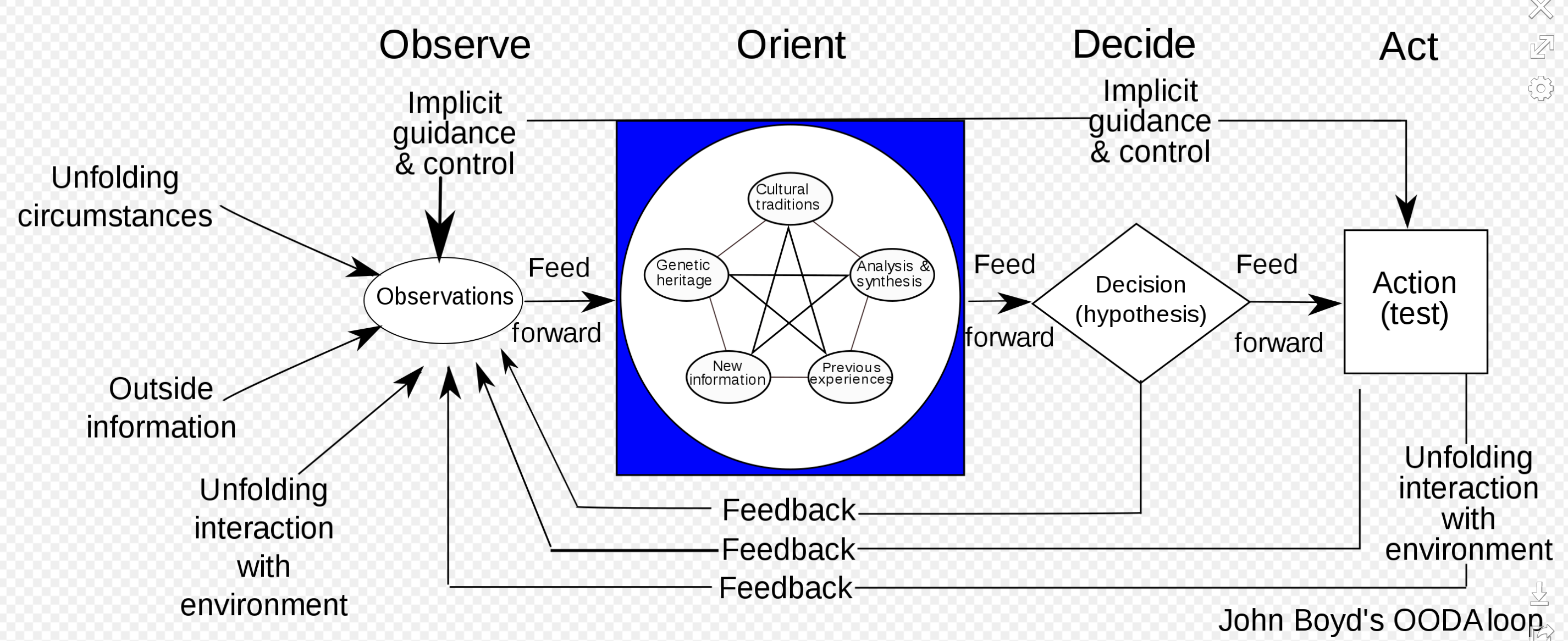
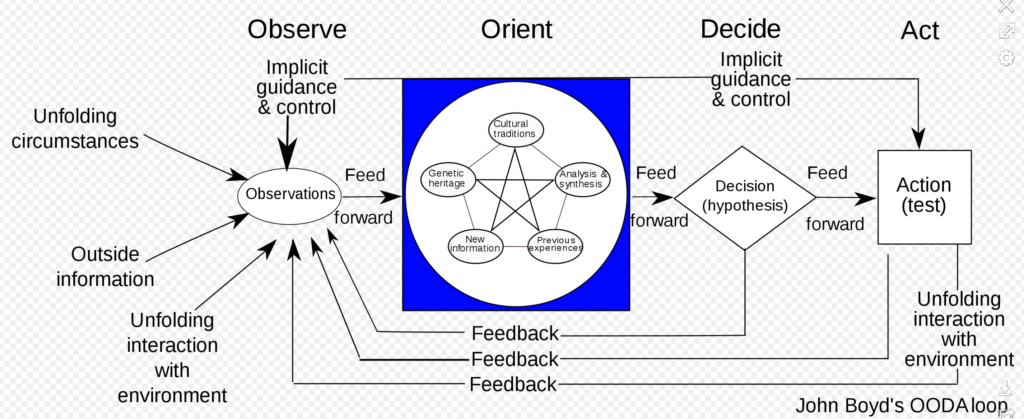
Through my work in the information security industry, I’ve come to appreciate a decision-making cycle created by military strategist and U.S. Air Force Colonel John Boyd called the OODA Loop (observe–orient–decide–act).
Mood Music:
It was designed as a combat operations process but has become more widely applied to commercial operations and learning processes. The basic idea is to use agility to overcome the raw power of opponents.
I’ve been fortunate in getting to know some super-smart people who use it for cyber security and, in the current environment, operations in a pandemic. The OODA Loop site, operated by OODA LLC founders Matt Devost and Bob Gourley, has become daily reading for me.
Lately, I’ve been taking this to the meta-personal level, trying to apply it to how I conduct myself daily and keep steady as a guy living in uncertain times with a mind sometimes hobbled by OCD, anxiety and depression.
I’m not sure if this is even a logical path. I’m hoping my friends in the OODA Loop realm will have comments about it after reading.
I’m using it against the raw power of the depressive and anxious effects of the current lockdown, which has fueled the potentially destructive side of my OCD and threatened to cripple me within the mental battlefield.
Observe: Since early January, I’ve kept a daily eye on the infection, recovery and death rates, as well as geographic spread. I’ve opted for emotionless data points from the likes of Worldometers. As the data has painted a picture of trajectory, my feelings have ranged from disbelief and denial to fear and uncertainty. Along with the useful data points are myriad articles that make predictions based on information that varies widely in levels of emotion and accuracy. This makes useful observation tricky.
Orient: By late February, as the data points showed a clearer picture of what by then was, to me, an inevitable pandemic, I started to work on adapting my brain to the idea that this would be a daily reality and that I’d have to keep being my best self as the world spiraled out of control. I doubled down on my exercise and food regimen, went from an originally planned 60-pound weight loss to 75 pounds (just about there now), and started to shift my daily research efforts to anything that would help clients stay running amid lockdowns and mass working from home (WFH).
Decide: About two days before my company moved to full WFH mode, I decided to quarantine from the office, at least. I had been to the RSA Conference in San Francisco a couple weeks before and news had just arrived that a couple attendees had contracted the virus, one of whom was gravely ill (he has since recovered, thank God). I was just shy of the two-week mark of returning home but didn’t want to chance becoming a risk to co-workers. In doing so, I was making a choice to hunker down for the long haul.
Act: Since then, I’ve done my damndest to stay healthy physically and mentally. I walk each morning and take afternoon drives. I’ve strived to do my job in the best ways possible, focusing on clear, step-by-step guidance to help clients protect the platforms and tools they currently rely on as everyone works from home — VPNs, videoconferencing, messaging — and I’ve used this blog to help keep the public discourse rational and hopeful while making note of coping mechanisms for those predisposed to mental disorders. I’ve stayed connected to friends through Zoom “happy hours.” I wear a mask and gloves when I have to go out.
When the constraints of being homebound make my temper boil over (I’m ashamed to admit I yelled and angrily slammed my iPhone down one night because a restaurant left something out of our takeout order — not my finest hour when dealing with a trivial, first-world problem) I’ve sought ways to release the pressure.
I’ve always favored hard rock music but in recent weeks my choices have veered to the heaviest end of the spectrum — including battle music from different TV shows and films. Today’s mood music is one example.

And I’ve found a simple, fun way to grind out feelings of angst. Erin got me a manual coffee bean grinder for Easter and I’ve found it’s good, aggressive fun to pace around the house while grinding beans.
I guess we’re never too old to learn new coping mechanisms, especially when sanity depends upon it.
Though I’m not at all certain I’m using the OODA Loop as intended, it has at least given me another way to keep fighting. I’m grateful.